IBM Invests in AI Cybersecurity for the Cloud with a Planned Acquisition of ReaQta
IBM expands open and automated cybersecurity offerings for the cloud with a new XDR platform.
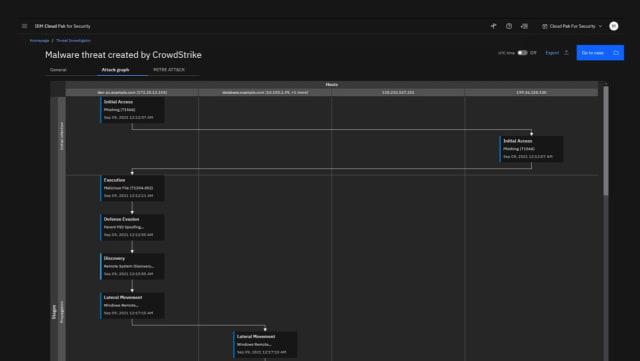
An example of the QRadar XDR interface with an automated malware threat detection program. (Image courtesy of IBM.)
To meet modern security needs, IBM recently announced its plans to acquire ReaQta, a data security company that uses artificial intelligence (AI) to automate the process of identifying and responding to cyber threats. As part of the announcement, IBM also described its new QRadar XDR suite of security software, which will include ReaQta’s offerings following the acquisition of the company.
The 2021 Cost of a Data Breach Report Highlights Complex and Expensive Threat Recovery Process
Each year, Ponemon Institute releases the Cost of a Data Breach report, sponsored and analyzed by IBM Security. For the 2021 report, the institute surveyed more than 500 organizations for their real-world experience with data breaches. The report detailed the increased complexity of modern data and security breaches, with the shift to remote operations during the pandemic increasing security costs by an average of 10 percent.
When it comes to data and security breaches, companies pay over $4 million per incident on average. This is the largest repair cost described in the 17-year history of the report. The report also found that the amount of time required to detect breaches is also increasing, with most companies unable to detect a breach for upwards of 212 days. The longer it takes to identify a breach, the more expensive and time-consuming it can be to determine the extent of damage and the repair requirements.
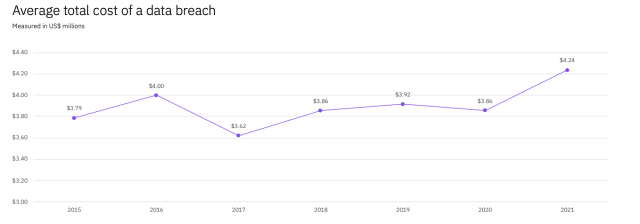
The average total cost for identifying and repairing a data breach hit the highest value on record in 2021. (Data courtesy of IBM.)
With the recent shift of employees working from home, IT environments are increasingly complex and dispersed. Multiple devices and users spanning remote, on-site and cloud-based operations can make identifying and responding to security threats challenging. The report found that data breaches cost an average of $1 million more when remote work was determined to factor in the incident.
Interestingly, the report found that modern approaches to data security surveillance and threat detection reduced costs for companies. For example, companies using AI, security analytics and encryption-based programs could reduce costs associated with a breach by more than $1 million on average.
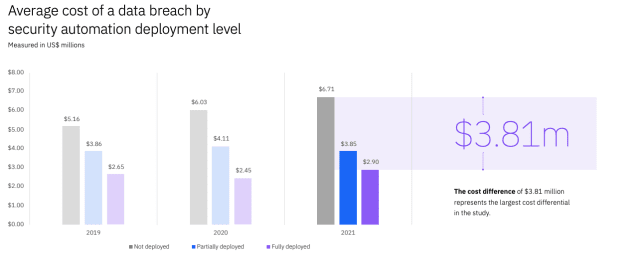
Companies employing AI-driven security solutions save more money on average regarding security threat detection and repair. (Data courtesy of IBM.)
“Higher data breach costs are yet another added expense for businesses in the wake of rapid technology shifts during the pandemic,” said Chris McCurdy, IBM Security vice president and general manager. “While data breach costs reached a record high over the past year, the report also showed positive signs about the impact of modern security tactics, such as AI, automation and the adoption of a zero-trust approach—which may pay off in reducing the cost of these incidents further down the line.”
IBM Acquires ReaQta to Expand AI Security Capabilities
A team of machine learning researchers, comprised of offensive and defensive cyber security experts, founded ReaQta. With their diverse expertise, the company built an active defense intelligence platform to provide clients with AI-driven detection and responses to security threats. Without needing additional data scientists, companies can use the platform to automate and simplify their overall security strategy without compromising quality. The unified, one-page workflow makes it streamlined to analyze and review all incidents.
The behavioral-based platform can identify and stop known and unknown security threats in real-time. By identifying normal behavior at each endpoint, the software can detect anomalous activity with a high degree of accuracy. The platform is also designed to be used in a hybrid model to protect on-site and cloud operations by strengthening companywide security. Deep learning within the AI system is done natively on the endpoint of the platform to help companies improve the definition of the threat behavior on each custom endpoint.
The anti-ransomware engine is optimized for high-load machines to avoid any slowdowns as threats are detected and eliminated. With a single sensor, the software takes up less than 1 percent of the CPU and can operate on all architectures without requiring an Internet connection.
“Our mission at ReaQta has been to better equip the defenders, who are tirelessly striving to stay ahead of cyber threats, with advanced technology to quickly identify and block new attacks,” said Alberto Pelliccione, ReaQta CEO. “Joining forces with IBM will enable us to enhance and scale our unique AI capabilities across all types of environments via a proven platform for threat detection and response.”
Advanced Threat Detection and Response with IBM QRadar XDR
Built on Cloud Pak for Security, IBM’s open, cloud-native security platform, the QRadar XDR is an all-in-one solution for threat detection, investigation and response. Companies using the XDR platform can speed up threat investigation 60 times thanks to an automated, AI-driven triage and contextual intelligence.
The benefit of an open XDR model is integrating solutions from multiple platforms in a unified workflow without moving any data. In contrast to other open programs, the QRadar XDR does not require IBM-specific applications and aligns with the Open Cybersecurity Alliance.
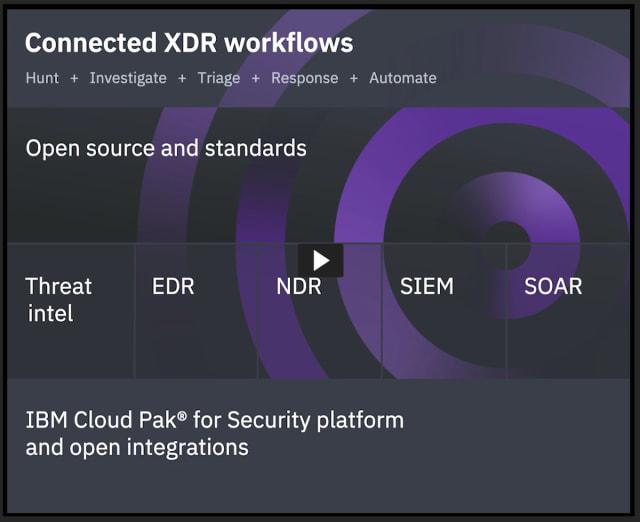
An overview of the IBM QRadar XDR platform. (Image courtesy of IBM.)
With the addition of ReaQta, the QRadar XDR suite will include endpoint detection and response (EDR). IBM will then have the ability to offer native capabilities for all XDR functions while also allowing third-party tools within their partner ecosystem. XDR Connect will enable companies to connect existing security toolsets, data and users to create one unified workflow for threat detection and response.
The XDR platform combines important inputs from EDR, security analytics, cloud workload and network data to develop a comprehensive portrait of potential security threats. It also automates root cause analysis and the process of recommending responses to help IT departments quickly make necessary repairs.
“Complexity has created a cloak that attackers are operating under, furthering their ability to circumvent defenders,” said Mary O'Brien, IBM Security general manager. “The future of security is open using technologies that can connect the security insights that are buried across disparate tools and advanced AI to identify and automatically respond to threats more quickly across their entire infrastructure, from endpoint to cloud. With our expanded capabilities via QRadar XDR and the planned addition of ReaQta, IBM is helping clients get ahead of attackers with the first XDR solution that reduces vendor lock-in via the use of open standards.”
Comprehensive Cyber Security Made Possible by AI
The power of machine learning is making the process of identifying and responding to security threats easier for companies without the requirement for advanced data science teams. To meet the needs of Industry 4.0, automated, AI-driven operations will need equally intelligent threat detection. AI-driven cybersecurity solutions can monitor millions of connected devices for incoming and outgoing traffic to identify suspicious activity in real-time. With consistent improvements to advanced cybersecurity solutions, open platforms will allow companies to invest in state-of-the-art threat detection and response software to protect their Internet of Things (IoT).